| implant/elevate/bypassuac_compdefaults |
Bypass UAC via registry hijack for ComputerDefaults.exe. |
| implant/elevate/bypassuac_compmgmtlauncher |
Bypass UAC via registry hijack for CompMgmtLauncher.exe. |
| implant/elevate/bypassuac_eventvwr |
Uses enigma0x3's eventvwr.exe exploit to bypass UAC on Windows 7, 8, and 10. |
| implant/elevate/bypassuac_fodhelper |
Bypass UAC via registry hijack for fodhelper.exe. |
| implant/elevate/bypassuac_sdclt |
Uses enigma0x3's sdclt.exe exploit to bypass UAC on Windows 10. |
| implant/elevate/bypassuac_slui |
Bypass UAC via registry hijack for slui.exe. |
| implant/elevate/system_createservice |
Elevate from administrative session to SYSTEM via SC.exe. |
| implant/fun/zombie |
Maxes volume and opens The Cranberries YouTube in a hidden window. |
| implant/fun/voice |
Plays a message over text-to-speech. |
| implant/gather/clipboard |
Retrieves the current content of the user clipboard. |
| implant/gather/comsvcs_lsass |
Utilizes comsvcs.dll to create a MiniDump of LSASS, parses with pypykatz. |
| implant/gather/enum_domain_info |
Retrieve information about the Windows domain. |
| implant/gather/hashdump_dc |
Domain controller hashes from the NTDS.dit file. |
| implant/gather/hashdump_sam |
Retrieves hashed passwords from the SAM hive. |
| implant/gather/loot_finder |
Finds loot on the target box. |
| implant/gather/user_hunter |
Locate users logged on to domain computers (using Dynamic Wrapper X). |
| implant/inject/mimikatz_dotnet2js |
Injects a reflective-loaded DLL to run powerkatz.dll (@tirannido DotNetToJS). |
| implant/inject/mimikatz_dynwrapx |
Injects a reflective-loaded DLL to run powerkatz.dll (using Dynamic Wrapper X). |
| implant/inject/mimikatz_tashlib |
Executes arbitrary shellcode using the TashLib COM object. (Work in Progress!) |
| implant/inject/shellcode_dotnet2js |
Executes arbitrary shellcode using the DotNet2JS technique. Inject shellcode into a host process via createremotethread as a new thread (thanks psmitty7373!). |
| implant/inject/shellcode_dynwrapx |
Executes arbitrary shellcode using the Dynamic Wrapper X COM object. |
| implant/inject/shellcode_excel |
Runs arbitrary shellcode payload (if Excel is installed). |
| implant/manage/enable_rdesktop |
Enables remote desktop on the target. |
| implant/manage/exec_cmd |
Run an arbitrary command on the target, and optionally receive the output. |
| implant/persist/add_user |
Adds a either a local or domain user. |
| implant/persist/registry |
Adds a Koadic stager payload in the registry. |
| implant/persist/schtasks |
Establishes persistence via a scheduled task. |
| implant/persist/wmi |
Creates persistence using a WMI subscription. |
| implant/phishing/password_box |
Prompt a user to enter their password. |
| implant/pivot/exec_psexec |
Run a command on another machine using psexec from sysinternals. |
| implant/pivot/exec_wmi |
Executes a command on another system. |
| implant/pivot/stage_wmi |
Hook a zombie on another machine using WMI. |
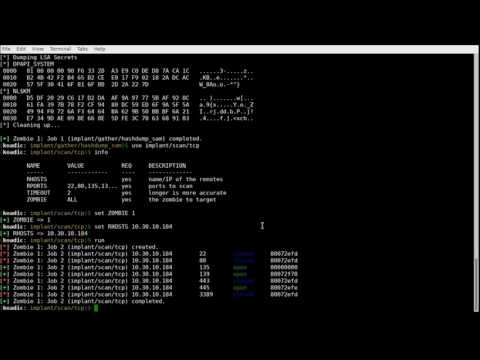
| implant/scan/tcp |
Uses HTTP to scan open TCP ports on the target zombie LAN. |
| implant/utils/download_file |
Downloads a file from the target zombie. |
| implant/utils/multi_module |
Run a number of implants in succession. |
| implant/utils/upload_file |
Uploads a file from the listening server to the target zombies. |
 客服电话
客服电话
 APP下载
APP下载

 官方微信
官方微信




















请发表评论